
Enabling Agility Without Sacrificing Security for DevOps
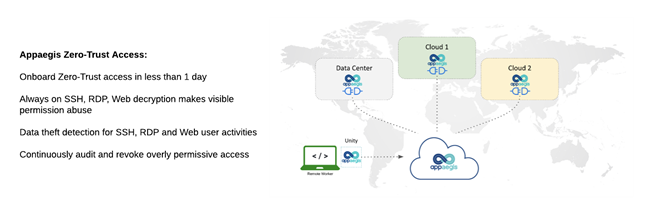
Maintaining a hybrid cloud infrastructure has become the norm for most organizations. This new architecture has forced organizations to rethink remote access strategies. They are migrating from a network-based policy access approach to identity-based access. In our recent update Appaegis introduced the Appaegis Unity Agent, to address this need.
The agent extends our already comprehensive zero-trust solution to help organizations close security gaps for SSH, RDP and Kubernetes access. Appaegis' Unity Agent is a lightweight agent available for Mac and Windows. It allows IT security to implement strict, role based, least privileged access to corporate resources.
These controls can be applied even when DevOps and NetOps engineers use local SSH and RDP clients. The Appaegis Unity Agent addresses the top concern in securing DevOps and NetOps access, without compromising agility. It prevents risky behaviors such as the use of shared and static passwords and keys.
Native Application Support for DevOps
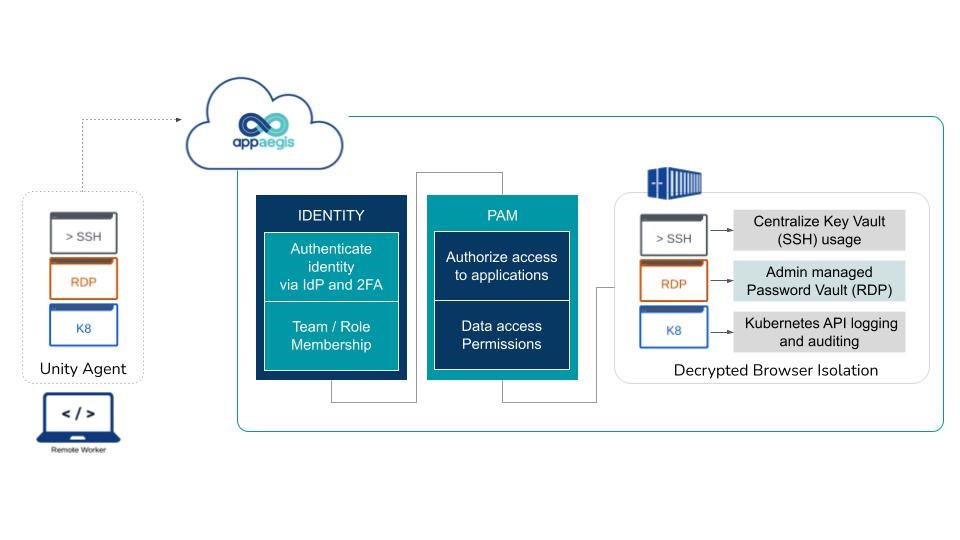
Appaegis’ agent, with its identity and permission-based access controls, simplifies and centralizes SSH and RDP access for hybrid cloud environments. It does that without impacting user experience.
By integrating with popular identity providers (IdP) and key vault services, we centralize access. This centralization enables secure access that requires the use of keys, without requiring passwords and key sharing. Malicious or accidental exposure of such keys increases the risks of data theft and disruption of business operations. Our approach eliminates the risk of sharing such keys and passwords which provide elevated privileged access.
Appaegis Unity Agent and our zero-trust approach to privileged access provides the dual benefit of increased security and operational efficiency. The increased security comes from closing security gaps. Greater operational efficiency comes from centralizing privileged access management for on-prem and cloud resources. The agent allows development engineers to utilize their local SSH and RDP terminals and clients.
The security gaps that we mitigate include:
- Preventing the use of shared and static passwords for SSH access
- Requiring 2-factor authentication for application access using SSH, RDP, and Kubernetes
- Implementing zero-trust least privileged access for SSH and RDP applications
- Detecting and preventing data theft with detailed visibility and control over user activity when accessing SSH and RDP applications
The operational benefits of centralizing access include:
- Access logging of Kubernetes API and Exec for auditing and compliance visibility
- Integration with the more popular key vault services (AWS KMS, HCP Vault, Azure Key Vault)
- Enabling creation of strict privileged access policies in minutes to onboard applications and users rapidly
- Allowing quick revocation of unneeded access or permissions and quick audit of privileges
Out of the box integration with multiple vendors and services for faster ROI and rapid implementation
|
Identity Providers (IdP) |
Key Vault Services |
|
Okta Azure AD Google Workspace |
HCP Azure Key Vault AWS KMS |
The launch of the agent is another step in providing a holistic solution that integrates the cloud into cloud access security! Appaegis IAC is built to secure access to applications, enhance data security, and implement a zero-trust security architecture. You can also read about our other recent updates.
Appaegis Unity Agent Feature Summary
With the Appaegis Unity Agent we have addressed the top concerns to securing DevOps and NetOps access in hybrid cloud environments. Most organizations have adopted hybrid cloud infrastructures. Organizations must implement solutions to enforce identity and permissions-based access, simplify onboarding and offboarding of users, for this new environment.
If you are looking for a solution that enable DevOps to securely access SSH, RDP and Kubernetes resources. Or want to learn about how Appaegis helps organizations enforce least privileged access to on-prem routers and switches. Click here to set up a meeting.

