We recently talked about helping our customers achieve SOC compliance. As our customers go through journey, we are committed to ensuring that our own products adhere to strict security guidelines and standards. To that end we have completed are SOC2 Type 1 certification and are well on our way to Type 2 certification. To ensure ease of compliance we continue to enhance our logging capabilities.
Below are more details on all of those developments.
1.SOC2 Type 1 Certification
Using products from any SaaS vendor involves trust. In a world where customer data is stored in the cloud, often controlled by the SaaS vendor, such trust must be earned. As part of earning that trust and protecting data vendors are ensuring that they comply with strict standards like SOC2.
Our security best practices often go beyond standards. SOC 2 Type 1 certification is a milestone that redoubles our commitment to ensuring that customer data stored in our cloud is protected by standards compliant processes. All of our processes and security profiles are now updated for SOC2 standards.
2. Enhancements to Audit Logging
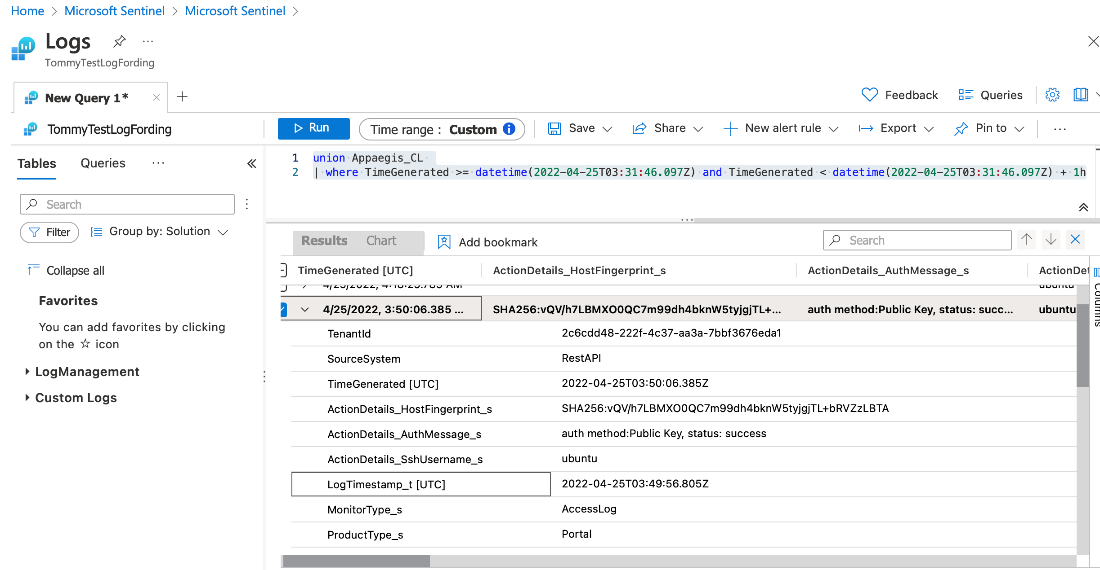
In our continued effort to provide greater visibility into every interaction between users and cloud infrastructure, we continue to enhance our Audit Logging capabilities. Appaegis has further improved the access logging capability for SSH, RDP, Kubernetes with additional context. We have also added the ability to forward the logs to Microsoft Sentinel so customers can perform custom data analytics
An example of logs forwarded to Microsoft Sentinel for an SSH session are shown below
If you or anyone else at your company would like to hear about our SOC 2 compliance journey, reach out to us. If you are looking for ongoing help in ensuring continued SOC 2 compliance, Appaegis Access Fabric can help! Click here to learn more about the capabilities of Appaegis Access Fabric.